Identity and Documents
Introduction
Document protection / fraud is a growing problem and demand utmost attention towards implementation of authentication technologies & solutions in eliminating fakes from system. Identity fraud is now the fastest growing crime in the US and accounts for half of all fraud in the UK.
The fraudulent reproduction of certificates has increased significantly in recent years, becoming a menace for many organizations. Fake certificates can be used to assist in illegal entry into the country, facilitating obtaining identity documents such as Voter ID / Aadhar Card, securing employment in fields for which an individual is not qualities, damaging the reputation of Governments and awarding bodies and possibly even placing the public at risk.
For example, the recent drive by Uttar Pradesh government found that as many as 3,000-4,000 teachers enrolled in the State’s Basic Education Department are found to have fake PAN numbers and educational qualification certificates. In another case, the alleged mastermind behind the September 13 serial blasts (2008) in India used a fake certificate from one top university in Uttar Pradesh to get admission in New Delhi. Now almost, after 12 years, the University has decided to secure their certificates and degrees.
Types of Document Frauds
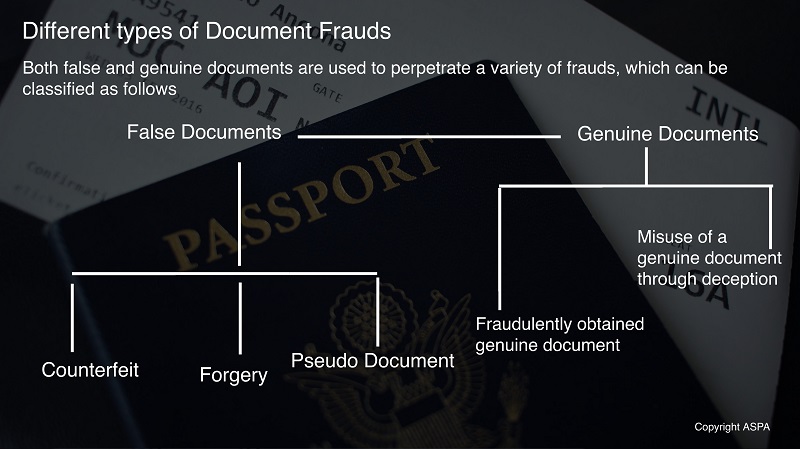
Both false and genuine documents are used to perpetrate a variety of frauds, which can be classified as follows:
- False documents
- Counterfeit – a document that constitutes an unauthorized reproduction of a genuine document. These documents are not legitimately manufactured, nor issued or recognized by an official authority.
- Forgery – these are typically based on a genuine document, a part of which has been added or altered in order to give misleading information about the person who presents it.
- Pseudo document – a document produced with no authority and which is not officially recognized. They can occur in various forms and may have the physical appearance of a passport or an ID card.
- Genuine documents
- Fraudulently obtained genuine document– an authentic identity or travel document obtained through deception by submission of either false or counterfeit documents, cooperation of a corrupt official or impersonation of the rightful holder of a genuine document.
- Misuse of a genuine document through deceptionby a person who knowingly misrepresents him or herself by using someone else’s identity or travel document. Often, the biographical details and photograph resemble the impostor, helping him or her to pass as the rightful bearer.
Reasons behind the document fraud cases
The lack of standardization, absence of authentication technologies, uniformity of database and transparency in systems, are the reasons behind the increase of fake documents. In most of the cases, the documents were easily copied in absence of anti-counterfeiting technologies as well as a system providing ease for cross-verification for verifying these documents. Counterfeiters are becoming successful because we are not making their task difficult. It is realistic to accept that given time, resources, and inclination, the integrity of any document can be compromised.
Even the most secure electronic ID documents are still subject to counterfeiting, particularly aspects of the material document, such as the cardholder’s image or other personalized information. All our PAN Card, Passport are recorded in digital repository, still we have them in physical format form for human verification in case of any digitization /e-failure. and for our record. In standard approach, the Universities and Institutions are using must secure their physical degrees with at-least five security features.
The Solution Integrated Approach
A secure design advocates collective defensive element as part of an integrated approach to document protection that involves design, printing technique, security ink and security paper to discourage fraudulent activity. When included at the design stage, security devices offer mutually protective elements that tend to resist counterfeit or forgery more effectively than by simply adding a security feature to an already existing document.
By layering a combination of multiple features into any given document, increased levels of security protection are achieved. Layering begins with a substrate, or specialized paper, that may itself contain protective features such as watermarks, chemical sensitive stains, invisible fibres and so on. Other subtle or covert elements such as “void” pantographs produce visible warnings when a document is scanned or copied. The images printed on the documents themselves may incorporate specialized covert or overt security inks, foils, microprinting, encoding, etc., all designed to make the job of unauthorized reproduction as great a challenge as possible.
Document Security Features – Standards review
Perfect document security is an unattainable goal. Security measures must be regarded as reducing the risks of forgery or unauthorised alteration or misuse, not eliminating those risks. The security features recommended below should be reviewed at regular intervals to keep pace with developments in technology and patterns of fraud. Increased sophistication in counterfeiting techniques may require features to be downgraded or removed.
Table (a) Document Security Categories and Features
| Security category | |||
|---|---|---|---|
| High | Medium | Standard | |
| Covert |
|
|
|
| Semi-covert |
|
|
|
| Overt |
|
|
|
| Integrated circuit |
|
||
*Covert represents the third line of document inspection. A specialist may be required to conduct a detailed in-depth examination of a document using special equipment and knowledge.
Semi-covert represents the second line of document examination. A trained employee using simple equipment such as a magnifying glass, ultra-violet light, infra-red lamp, etc.
Overt represents the first line of document examination undertaken by a trained employee using sight and/or touch.