Digital Authentication
A robust digital-authentication program can help prevent fake products from entering the supply chain, providing a key complement to the benefits of overt and covert technologies. While physical technologies are essential for protecting product label & packaging, the recent advancement in digital technologies has opened new ways for brands/authorities in traceability which further support functions including authentication, monitoring the supply chain & data intelligence.
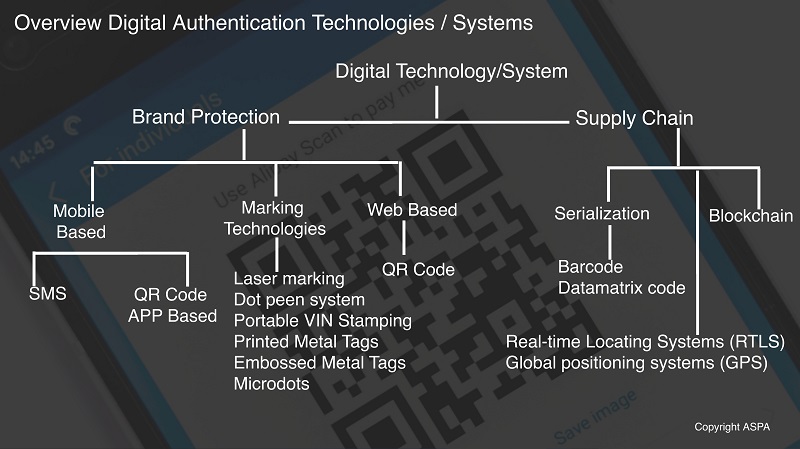
Digital technologies may be either overt or covert, but all require an electronic means for detection and validation either mobile or web-based application. These can be classified in two key categories.
- Digital Brand Protection Technologies
- Digital Traceability Technologies in Supply Chains
- Online Brand Monitoring Technologies
Digital Brand Protection Technologies:
- SMS based Brand Protection: Mobile Product Authentication service includes a scratch-off label affixed to product packaging or alphanumeric code printed on the product packaging. These codes can be checked with simply SMS to a mobile number printed on the pack. In return, the consumer received a message providing the authenticity of the product. These codes can be printed using inkjet or laser printers or applied via labels that may include one or more physical security features.
- RFID/NFC Tags: With these technologies Brand can convert their label into smart & intelligent devices, strengthening brand connection, enhancing supply chain efficiencies, greater design flexibility, as well as higher effective consumer engagement. For example, last year in USA Malibu deployed 300,000 connected bottles in the states of Ohio and Texas as part of the campaign the MalibuGames 2019 (see the image).
Digital Traceability Technologies in Supply Chains: For the supply chain requirements, unique coding (also known as serialization) technologies track and trace objects, products, assets, and individuals through-out the value chain by capturing and transferring data. They can provide the essential information (e.g., location, vibration, temperature, humidity, arriving time, speed, and vehicle status) in an automated and timely manner which enables detection of counterfeits or diversion of genuine goods into the grey market. While there are several technologies involved in automated tracking, the most used technologies are:
- Barcodes/Data-Matrix Codes
- Radio Frequency Identification (RFID)
- Real-time Locating Systems (RTLS), and
- Global positioning systems (GPS)
Smart coding takes a basic lot or batch code further by altering and verifying specific characters in the code, making it more difficult for unauthorized parties to copy. Smart codes are difficult to emulate by unintended third parties and are an important foundation for an effective counterfeit prevention system.
Online Brand Protection Technologies: One of the challenges in the online world is that it is easy for fraudsters to hide their identity and make it harder for brand owners to detect who is behind all the brand abuse. Once you have identified your High-Value Target, the online brand protection tools & services help you in providing more detail and information about these egregious offenders. To accomplish this, cyber investigators use proprietary data sources and advanced technology. Moreover, they can also perform controlled test purchases to find counterfeits. The data can also be used for further intelligence and shared with law enforcement.
All these technologies can be checked with mobile or web-based tools and applications and provide real-time information based on algorithms and artificial intelligence. In terms of overall systems from these technologies, one can further build private or blockchain-based platforms. There are various Authentication/traceability technologies, solutions and systems are available across the globe. All technologies are good, perhaps, it is important to understand the strengths and limitations inherent to different technologies. It is important to understand how to protect the product & its packaging from physical attack as well as maintaining a secure supply chain. The layered approach is always better.
For more information, understanding physical authentication solutions, click here
For more information, on selecting authentication solutions, click here
For more information regarding solutions according to particular industry, visit the industries section.